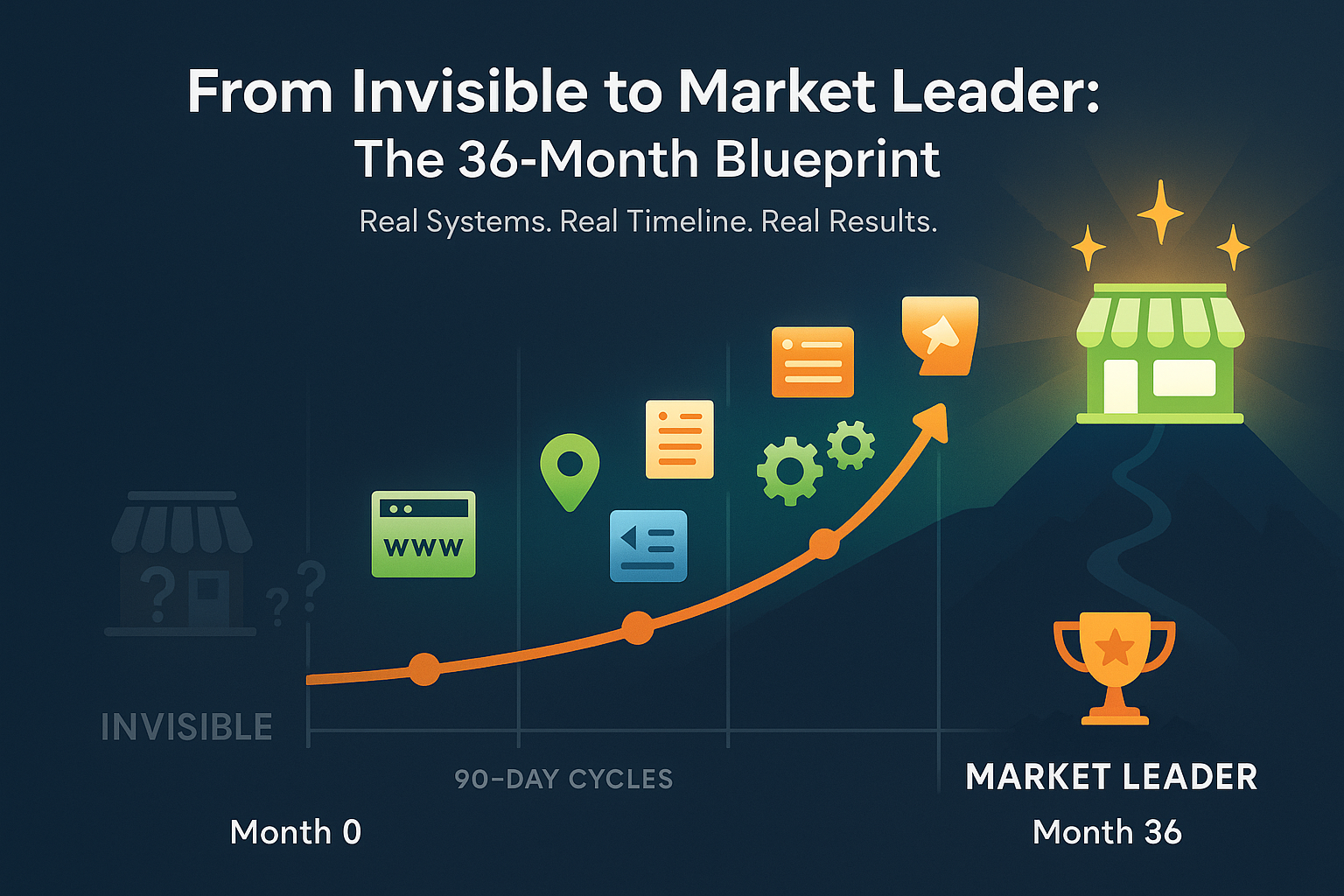
AI Coding Tools vs. System Engineering: The Real Gap – What the Redis Creator’s Latest Post Reveals About AI and Professional Development in 2025
AI can write code. But building secure, scalable systems that businesses can trust? That takes system engineering. At MosierData, we blend AI speed with decades of system architecture experience, because reliability still matters.