From Virtually Invisible to Market Leader in 36 Months: The Complete Digital Growth Blueprint
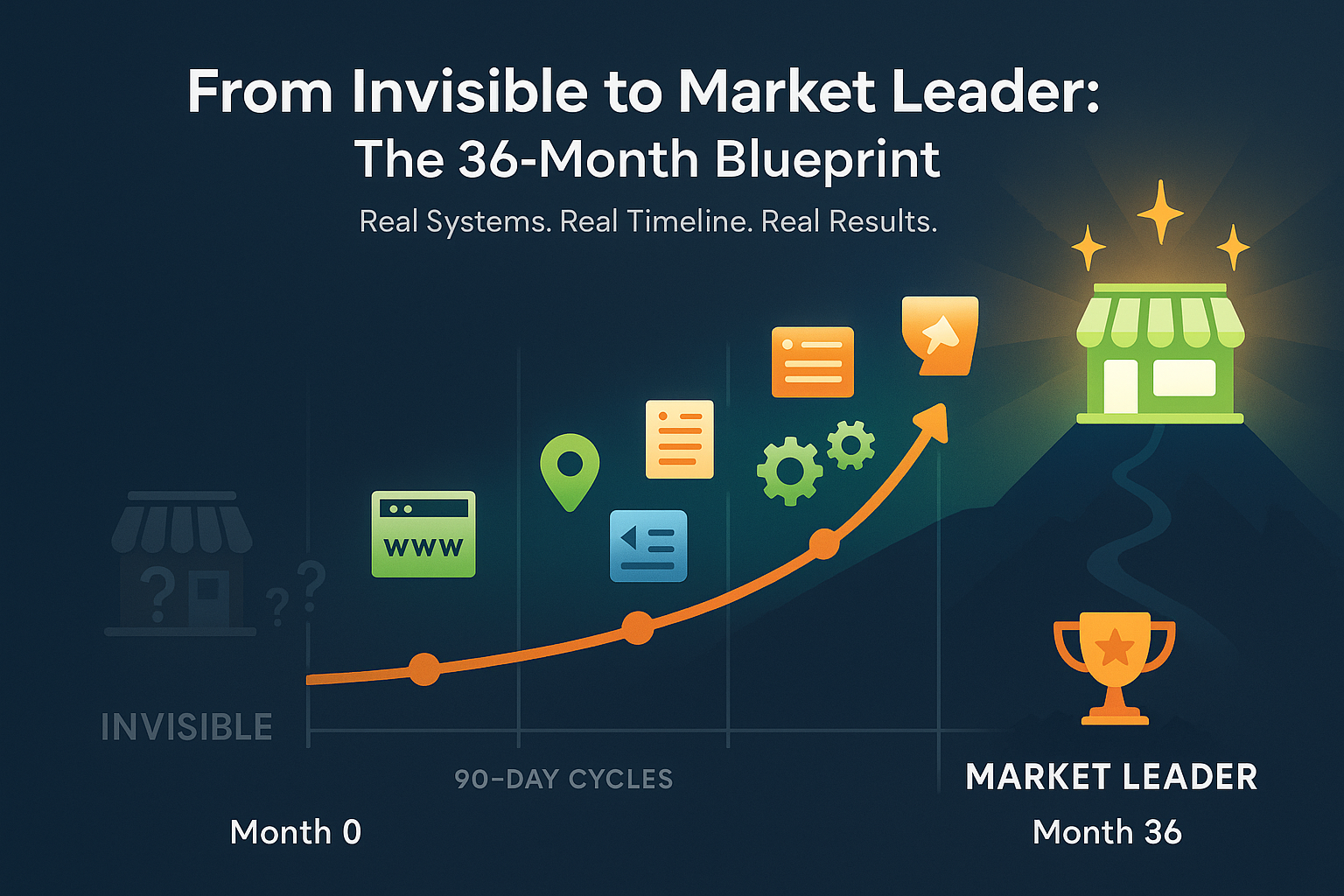
From invisible to market leader takes exactly 36 months. Not because we’re slow—because that’s how long it takes to build something that lasts.
12 months to build a foundation algorithms and humans trust. 12 months to prove the model and add amplification. 12 months to establish dominance through automation and AI.
You can’t skip steps. You can’t buy your way to the end. But if you approach it strategically—building in 90-day cycles, integrating every element—you build sustainable competitive advantages.
This isn’t just marketing. This is transformation.